To tell if someone is remotely accessing your iPhone, you need to check for unrecognizable devices signed in under your Apple ID. First, sign in to your Apple ID using your iPhone, then select Devices from the Settings menu. Scroll down the device list, and try to recognize any unauthorized device.
If you find any unrecognized device you can suspect it as a foreign device that can access your iPhone remotely.
Today’s tutorial discusses several methods to address remote devices attempting to access your iPhone. Moreover, you will find preventive solutions to block these remote and unauthorized access to your device.
Let’s have a deep dive!
Contents
- Remotely Access to iPhone- What Does It Mean?
- 7 Signs to Consider if Someone Accesses an iPhone Remotely
- How to Tell if Someone is Accessing Your iPhone Remotely?
- See Signed-in Devices:
- Steps to Remove a Device Using an iPhone:
- Unexpected Face or Touch ID:
- Steps to Change Face ID Security:
- Steps to Change Fingerprint Security:
- Check Two-factor Authentication:
- Steps to Turn on Two-factor Authentication:
- Review Apple ID:
- Steps to Review an Apple ID:
- Investigate Installed Apps:
- Frequently Asked Questions – FAQs
- Bottom Line
Remotely Access to iPhone- What Does It Mean?
An intruder can remotely control an iPhone or iPad through unauthorized access to an Apple Account. It lets hackers disclose all hidden passwords and credentials that harm personal or financial privacies.
This is different than Apple’s paternal control features. Apple is aware enough of its iOS devices’ security and privacy. Nevertheless, unsolicited access may happen remotely by hackers. It may cause severe safety threats to sensitive data and private contents.

Hackers can remotely handle an iPhone’s whole operations and applications after accessing it. They can control an iPhone with sophisticated spying tools and applications. And it is apparently unnoticeable by iPhone users in general unless they recognize the signs and effects.
7 Signs to Consider if Someone Accesses an iPhone Remotely
If someone gets remote access to an iPhone, it exposes some signs in its applications and settings. Let’s see what symbols usually appear on an iPhone due to authorized monitoring or controlling.
1. Unexpected Notifications
The remotely controlled or hacked devices receive unusual emails, messages, and notifications. If it happens on your iPhone, think again about your security & privacy.
2. Irregular Password Changes
If someone remotely accessed your iPhone, you can experience unexpected password changes on social media or other accounts. Of course, you don’t initiate these changes to your accounts.
3. Operational Disorders
unsolicited remote access occurs to functional disorders to iPhones. For example, you may experience higher data usage, unusual crashes, unexpected shutting downs, and more.
4. Slower Functioning
An iPhone gets slower in functioning with unauthorized apps and settings. And it may happen if somebody accesses and controls the device remotely.
5. Unusual Heating
You might experience unusual overheating of your iPhone if someone hacks or accesses it remotely. Though you are not excessively operating your device, it gets constantly overheated.
6. Quick Battery Drain
If someone remotely uses your iPhone, its battery drains rapidly, which seems unusual. And you see the battery power shortage, even if you don’t use your device.
7. Access Denial
The bitter experience may occur on an iPhone through access denial to essential sites and accounts. An intruder can control your access to particular social networking, personal, and financial sites.
Undoubtedly, unauthorized access to an iPhone may expose more signs than I have mentioned here. However, these are the symbols, to a large extent, that concern remote access to an iPhone.
How to Tell if Someone is Accessing Your iPhone Remotely?
Apple Support believes in the maximum security of its devices. Therefore, the iOS operating system has updated its user guides and privacy settings. If your iPhone is of iOS 15 or earlier, go through the checklists to understand if someone is remotely accessing your device.
See Signed-in Devices:
Find the devices available on your Apple account. If you find any unrecognized device logged in, it might be a foreign device that can control your host iPhone.
Solution:
Go to the settings of your iPhone and tap your name to find the devices that are available to your Apple ID. Remove the device from your Apple account If you can recognize any unauthorized access.
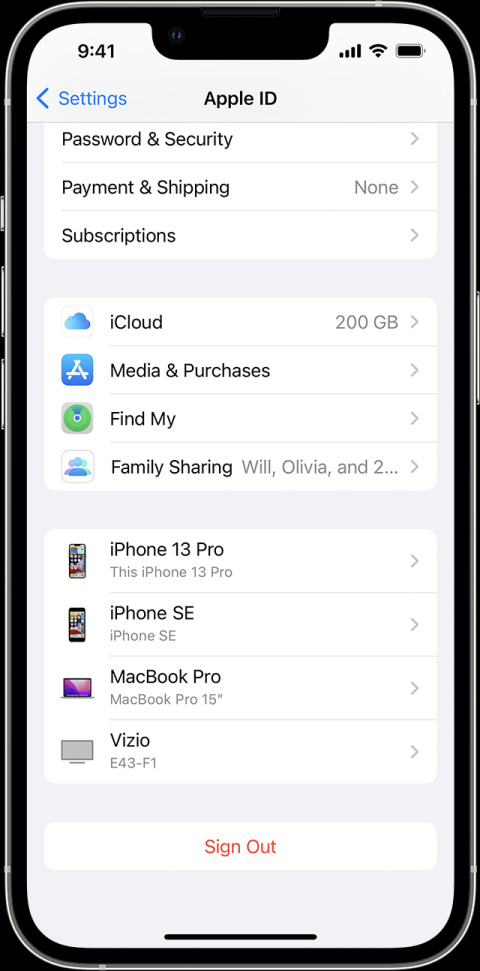
Steps to Remove a Device Using an iPhone:
Log in with your Apple ID and select the unrecognized devices. Tap the device in the list, see details of the device and click on remove from account. That’s it!
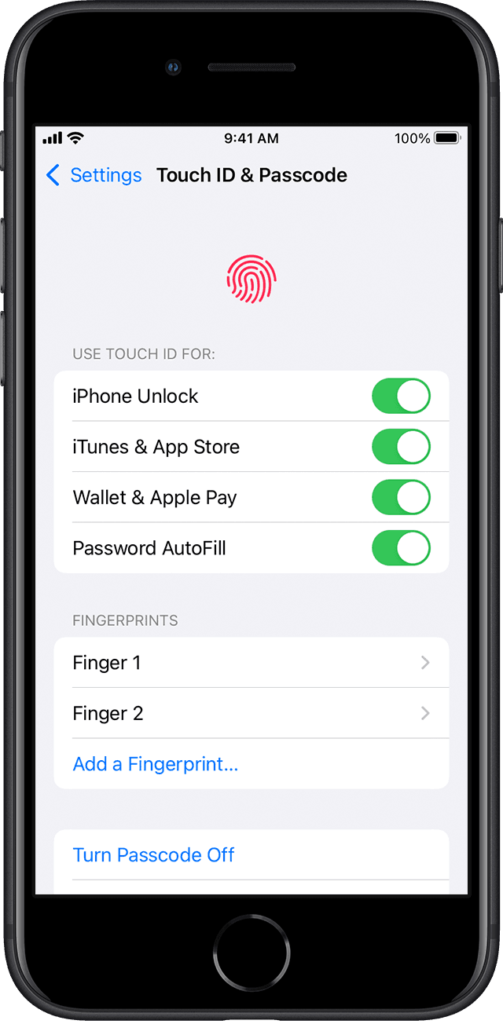
Unexpected Face or Touch ID:
If you see that an additional has replaced your preset Face or fingerprint ID, you can consider it a possible remote accessing sign.
Solution:
Check any unexpected Face ID or additional fingerprint security ID on your iPhone and replace them with a new Face ID or fingerprint security ID. It will protect your iPhone from remote access.
Steps to Change Face ID Security:
Go to settings > set up face ID and hold your device at portrait orientation. Place your face inside the frame and move your head gently and wait for the circle to be completed. Now finish face ID scan, hit continue, complete the circle move your head for the second time and click done.
Steps to Change Fingerprint Security:
Open the settings of your iPhone, tap touch ID and passcode, and enter your iPhone passcode. Now select Delete existing fingerprint from the menu and tap add a fingerprint. Follow the onscreen instructions to set up a new fingerprint.
Check Two-factor Authentication:
Care about two-factor authentication on your iPhone to understand whether someone is trying to breach your iPhone’s security. If you find any notification from an unauthorized device to authenticate, don’t ignore the signs of remote access.
Solution:
Use two-factor authentication and recognize whether the device is unauthorized before authenticating. Verify text messages or phone calls to permit any device to your iPhone.
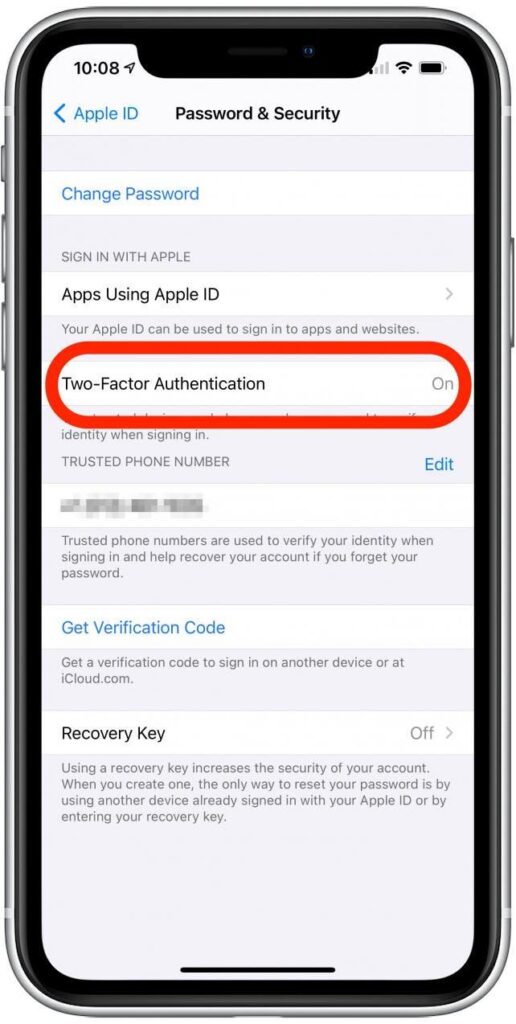
Steps to Turn on Two-factor Authentication:
From your iPhone’s home screen, go to settings > iCloud > iCloud profile name > password & security. Now select the turn-on two-factor authentication option. You’ll be asked to select your country and enter your phone number.
Now type in the code received to your phone message. Once you’ve successfully verified your number, type your Apple ID & password. That’s it! You’ve enabled two-factor authentication.
However, the steps can vary with Apple’s recent updates.
Review Apple ID:
See your security information on your Apple ID to find any more missing or adding to the account. If you get any mismanagement there, it can be an exposure to remote access.
Solution:
Log in to your Apple account and review all security information to see if someone has access to your iPhone remotely. You may change your Apple user ID and password to prevent such intrusion.
Steps to Review an Apple ID:
Open your phone’s settings app, log in with your Apple ID, and select review your ID details. Find and fix any intrusion if it happens there. If Apple doesn’t show any issues that need fixing, you’re all set.
Investigate Installed Apps:
Review all installed apps on your iPhone to check if there are any unfamiliar apps that look unsolicited.Try to find the source and purpose of these apps that you cannot remember.
Solution:
Go to the iOS App Store and investigate and review all the unfamiliar apps installed on your iPhone. If any app seems security-threatening, delete it from your device.
Frequently Asked Questions – FAQs
Tons of questions can arise in your mind when your iPhone is under unsolicited control by someone remote. Let’s learn more about the personal safety user guide for iOS devices.
How to immediately stop all sharing and access during security risk?
You can immediately stop all sharing and access of your iPhone with apps or people when your security is at risk by hackers or intruders. Here, the ways are to prevent all sharing and access to unsolicited users.
- Go to the safety check interface of your iPhone and use an emergency reset to hold all sharing and access to people or apps immediately. Moreover, it lets you review your account security features.
- Customize your sharing with people or apps by using the “manage and sharing settings” of your iPhone. The safety check option empowers you to fix what to share with whom for security purposes.
Important: If you use ‘emergency reset’ or ‘manage and sharing settings’ to stop sharing and access, the previously shared data, photos, and notes will be unavailable.
How to see if any app is remotely accessing my iPhone?
Someone can remotely access your iPhone using sophisticated apps installed on your device. It lets an intruder use camera, data, location, and more without the device owner’s permission. Turn on the app privacy report to tackle such unauthorized access.
Here is how to turn on the app privacy report!
- Go to the settings of your iPhone and tap privacy.
- Get down and tap the App Privacy Report.
- Now, click the Turn on App Privacy Report and let your device prevent unauthorized app access.
You can review the encrypted data gathered in the app privacy report to understand particular apps’ behavior on your device’s sensitive data and settings. Moreover, you can generate for the past 7 days.
Bottom Line
Apple promises to prevent unsolicited access to its iOS systems for users’ security and privacy issues. Nevertheless, intruders can access an iPhone, iPad, or iPod with sophisticated software or data theft.
Although it’s quite rare, virus attacks on your iPhone can give remote access to hackers. Make sure not to share your Apple ID and password with anyone or any website to prevent data theft.
